Review the Ipv6 Addressing Scheme Used in the Network Shown in the Following Figure
Chapter 2 Planning an IPv4 Addressing Scheme (Tasks)
This chapter describes the issues yous must resolve in order to create your network in an organized, toll-effective mode. After y'all resolve these issues, you tin devise a network plan as you configure and administrate your network in the future.
This chapter contains the post-obit information:
-
Determining the Network Hardware
-
Obtaining Your Network'due south IP Number
-
Deciding on an IP Addressing Format for Your Network
-
Naming Entities on Your Network
-
Planning for Routers on Your Network
For tasks for configuring a network, refer to Chapter five, Configuring TCP/IP Network Services and IPv4 Addressing (Tasks).
Network Planning (Job Map)
| Chore | Description | For Information |
|---|---|---|
| i. Plan your hardware requirements and network topology | Determine the types of equipment that y'all demand and the layout of this equipment at your site. |
|
| 2. Obtain a registered IP address for your network | Your network must have a unique IP address if you programme to communicate outside your local network, for example, over the Net. | Refer to Obtaining Your Network's IP Number. |
| 3. Devise an IP addressing scheme for your systems, based on your IPv4 network prefix or IPv6 site prefix. | Determine how addresses are to be deployed at your site. | Refer to Designing an IPv4 Addressing Scheme or refer to Preparing an IPv6 Addressing Programme. |
| four. Create a listing that contains the IP addresses and host names of all machines on your network. | Utilise the list to build network databases | Refer to Network Databases |
| 5. Determine which proper name service to use on your network. | Determine whether to employ NIS, LDAP, DNS, or the network databases in the local /etc directory. | Refer to Selecting a Proper name Service and Directory Service |
| 6. Found authoritative subdivisions, if appropriate for your network | Decide if your site requires that you divide your network into administrative subdivisions | Refer to Authoritative Subdivisions |
| seven. Make up one's mind where to place routers in the network design. | If your network is large enough to crave routers, create a network topology that supports them. | Refer to Planning for Routers on Your Network |
| viii. If required, design a strategy for subnets. | You might need to create subnets for administering your IP address space or to make more IP addresses available for users. | For IPv4 subnet planning, refer to What Is Subnetting? For IPv6 subnet planning, refer to Creating a Numbering Scheme for Subnets |
Determining the Network Hardware
When you design your network, you must decide what blazon of network best meets the needs of your system. Some of the planning decisions you must brand involve the following network hardware:
-
The network topology, the layout, and connections of the network hardware
-
The number of host systems your network can support
-
The types of hosts that the network supports
-
The types of servers that you might need
-
The blazon of network media to employ: Ethernet, Token Ring, FDDI, and then on
-
Whether y'all need bridges or routers extend this media or connect the local network to external networks
-
Whether some systems demand separately purchased interfaces in addition to their built in interfaces
Based on these factors, you tin can determine the size of your local area network.
Note –
How you plan the network hardware is outside the scope of this manual. For assistance, refer to the manuals that come with your hardware.
Deciding on an IP Addressing Format for Your Network
The number of systems that yous look to support affects how you lot configure your network. Your system might require a small network of several dozen standalone systems that are located on one floor of a unmarried edifice. Alternatively, you might demand to set upward a network with more than one,000 systems in several buildings. This setup can require you to further divide your network into subdivisions that are called subnets.
When you plan your network addressing scheme, consider the post-obit factors:
-
The type of IP address that you want to use: IPv4 or IPv6
-
The number of potential systems on your network
-
The number of systems that are multihomed or routers, which require an IP address for each interface
-
Whether to use individual addresses on your network
-
Whether to have a DHCP server that manages pools of IPv4 addresses
The worldwide growth of the Cyberspace since 1990 has resulted in a shortage of available IP addresses. To remedy this situation, the Internet Applied science Task Force (IETF) has developed a number of IP addressing alternatives. Types of IP addresses in utilise today include the post-obit:
If your organization has been assigned more than than one IP address for your network or uses subnets, appoint a centralized authority within your organization to assign network IP addresses. That authority should maintain control of a pool of assigned network IP addresses, and assign network, subnet, and host addresses as required. To foreclose issues, ensure that duplicate or random network numbers practice not exist in your organization.
IPv4 Addresses
These 32-bit addresses are the original IP addressing format that was designed for TCP/IP. Originally, IP networks have three classes, A, B, and C. The network number that is assigned to a network reflects this class designation plus viii or more bits to represent a host. Course-based IPv4 addresses require you to configure a netmask for the network number. Furthermore, to make more addresses available for systems on the local network, these addresses were ofttimes divided into subnets.
Today, IP addresses are referred to every bit IPv4 addresses. Although you tin no longer obtain class-based IPv4 network numbers from an Internet access provider, many existing networks still take them. For more information about administering IPv4 addresses, refer to Designing Your IPv4 Addressing Scheme.
IPv4 Addresses in CIDR Format
The IETF has developed Classless Inter-Domain Routing (CIDR) addresses as a short to medium term fix for the shortage of IPv4 addresses. In add-on, CIDR format was designed every bit a remedy to the lack of capacity of the global Internet routing tables. An IPv4 address with CIDR notation is 32 bits in length and has the same dotted decimal format. Even so, CIDR adds a prefix designation later the rightmost byte to define the network portion of the IPv4 address. For more information, refer to Designing Your CIDR IPv4 Addressing Scheme.
DHCP Addresses
The Dynamic Host Configuration Protocol (DHCP) protocol enables a system to receive configuration information from a DHCP server, including an IP address, as part of the booting process. DHCP servers maintain pools of IP address from which to assign addresses to DHCP clients. A site that uses DHCP tin can use a smaller pool of IP addresses than would be needed if all clients were assigned a permanent IP address. You can prepare up the Solaris DHCP service to manage your site's IP addresses, or a portion of the addresses. For more information, refer to Chapter eleven, Near Solaris DHCP (Overview).
IPv6 Addresses
The IETF has deployed 128–bit IPv6 addresses every bit the long term solution to the shortage of available IPv4 addresses. IPv6 addresses provide greater address space than is available with IPv4. The Solaris OS supports IPv4 and IPv6 addressing on the same host, through the use of dual-stack TCP/IP. Every bit with IPv4 addresses in CIDR format, IPv6 addresses take no notion of network classes or netmasks. As in CIDR, IPv6 addresses use prefixes to designate the portion of the address that defines the site'due south network. For an introduction to IPv6, refer to IPv6 Addressing Overview.
Private Addresses and Documentation Prefixes
The IANA has reserved a block of IPv4 addresses and an IPv6 site prefix for use on private networks. Y'all can deploy these addresses on systems within an enterprise network but exist aware that packets with private addresses cannot exist routed across the Internet. For more information on private addresses, refer to Using Private IPv4 Addresses.
Note –
Private IPv4 addresses are also reserved for documentation purposes. The examples in this volume employ private IPv4 addresses and the reserved IPv6 documentation prefix.
Obtaining Your Network'due south IP Number
An IPv4 network is defined by a combination of an IPv4 network number plus a network mask, or netmask. An IPv6 network is defined by its site prefix, and, if subnetted, its subnet prefix.
Unless your network plans to exist private in perpetuity, your local users about likely need to communicate beyond the local network. Therefore, you must obtain a registered IP number for your network from the appropriate organization before your network can communicate externally. This address becomes the network number for your IPv4 addressing scheme or the site prefix for your IPv6 addressing scheme.
Cyberspace Service Providers provide IP addresses for networks with pricing that is based on unlike levels of service. Investigate with various ISPs to determine which provides the all-time service for your network. ISP's typically offer dynamically allocated addresses or static IP addresses to businesses. Some ISPs offer both IPv4 and IPv6 addresses.
If your site is an Internet service provider, yous obtain IP address blocks for your customers from the Internet Registry (IR) for your locale. The Internet Assigned Numbers Dominance (IANA) is ultimately responsible for delegating registered IP addresses to IRs effectually the globe. Each IR has registration information and templates for the locale that the IR services. For information most the IANA and its IRs, refer to the IANA'south IP Address Service page.
Note –
Do not arbitrarily assign IP addresses to your network, even if you are non currently attaching the network to external TCP/IP networks. Instead, use private addresses as described in Using Private IPv4 Addresses.
Designing an IPv4 Addressing Scheme
Note –
For IPv6 address planning information, refer to Preparing an IPv6 Addressing Program.
This department gives an overview IPv4 addressing to aid you in designing an IPv4 addressing plan. For information on IPv6 addresses, see IPv6 Addressing Overview. For information on DHCP addresses, see Chapter 11, About Solaris DHCP (Overview).
Each IPv4-based network must have the post-obit:
-
A unique network number that is assigned by either an ISP, an IR, or, for older networks, registered by the IANA. If yous program to use private addresses, the network numbers you devise must exist unique within your organization.
-
Unique IPv4 addresses for the interfaces of every organisation on the network.
-
A network mask.
The IPv4 address is a 32-bit number that uniquely identifies a network interface on a system, as explained in How IP Addresses Apply to Network Interfaces. An IPv4 address is written in decimal digits, divided into iv eight-scrap fields that are separated past periods. Each eight-chip field represents a byte of the IPv4 address. This form of representing the bytes of an IPv4 accost is oft referred to equally the dotted-decimal format.
The post-obit figure shows the component parts of an IPv4 address, 172.16.50.56.
Effigy 2–1 IPv4 Address Format
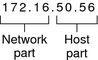
- 172.16
-
Registered IPv4 network number. In grade-based IPv4 notation, this number also defines the IP network grade, Class B in this instance, that would accept been registered by the IANA.
- 50.56
-
Host part of the IPv4 accost. The host part uniquely identifies an interface on a organisation on a network. Note that for each interface on a local network, the network part of the accost is the same, but the host part must be different.
If you lot plan to subnet a class-based IPv4 network, you demand to ascertain a subnet mask, or netmask, as explained in netmasks Database.
The side by side instance shows of the CIDR format accost 192.168.3.56/22
Effigy 2–2 CIDR Format IPv4 Address
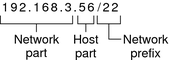
- 192.168.3
-
Network part, which consists of the IPv4 network number that is received from an Internet service provider or IR.
- 56
-
Host part, which you assign to an interface on a system.
- /22
-
Network prefix, which defines how many bits of the address comprise the network number. The network prefix also provides the subnet mask for the IP address. Network prefixes are also assigned by the Isp or IR.
A Solaris-based network can combine standard IPv4 addresses, CIDR format IPv4 addresses, DHCP addresses, IPv6 addresses, and individual IPv4 addresses.
Designing Your IPv4 Addressing Scheme
This department describes the classes into which standard IPv4 address are organized. Though the IANA no longer gives out course-based network numbers, these network numbers are still in use on many networks. Y'all might demand to administer the address space for a site with class-based network numbers. For a complete discussion of IPv4 network classes, refer to Network Classes.
The following table shows the division of the standard IPv4 address into network and host address spaces. For each grade, "Range" specifies the range of decimal values for the start byte of the network number. "Network Address" indicates the number of bytes of the IPv4 address that are defended to the network office of the address. Each byte is represented by xxx. "Host Address" indicates the number of bytes that are dedicated to the host part of the accost. For case, in a form A network address, the first byte is dedicated to the network, and the last iii bytes are dedicated to the host. The opposite designation is true for a class C network.
Table ii–1 Division of the IPv4 Classes
| Class | Byte Range | Network Number | Host Address |
|---|---|---|---|
| A | 0–127 | xxx | xxx.xxx.xxx |
| B | 128–191 | xxx.30 | 30.xxx |
| C | 192–223 | xxx.xxx.xxx | 20 x |
The numbers in the first byte of the IPv4 address define whether the network is grade A, B, or C. The remaining iii bytes have a range from 0–255. The two numbers 0 and 255 are reserved. You can assign the numbers i–254 to each byte, depending on the network class that was assigned to your network by the IANA.
The post-obit tabular array shows which bytes of the IPv4 accost are assigned to you. The table too shows the range of numbers inside each byte that are available for you lot to assign to your hosts.
Table 2–2 Range of Available IPv4 Classes
| Network Class | Byte 1 Range | Byte ii Range | Byte 3 Range | Byte 4 Range |
|---|---|---|---|---|
| A | 0–127 | one–254 | 1–254 | ane–254 |
| B | 128–191 | Preassigned by IANA | 1–254 | 1–254 |
| C | 192–223 | Preassigned by IANA | Preassigned past IANA | 1–254 |
IPv4 Subnet Number
Local networks with large numbers of hosts are sometimes divided into subnets. If you lot divide your IPv4 network number into subnets, you need to assign a network identifier to each subnet. You tin maximize the efficiency of the IPv4 address infinite by using some of the bits from the host part of the IPv4 accost as a network identifier. When used as a network identifier, the specified part of the address becomes the subnet number. Y'all create a subnet number by using a netmask, which is a bitmask that selects the network and subnet parts of an IPv4 address. Refer to Creating the Network Mask for IPv4 Addresses for details.
Designing Your CIDR IPv4 Addressing Scheme
The network classes that originally constituted IPv4 are no longer in utilise on the global Internet. Today, the IANA distributes classless CIDR format addresses to its registries around the world. Whatsoever IPv4 address that you obtain from an Internet access provider is in CIDR format, as shown in Figure 2–2.
The network prefix of the CIDR accost indicates how many IPv4 addresses are available for hosts on your network. Note that these host addresses are assigned to interfaces on a host. If a host has more than one physical interface, yous need to assign a host address for every concrete interface that is in use.
The network prefix of a CIDR accost too defines the length of the subnet mask. Most Solaris ten commands recognize the CIDR prefix designation of a network'southward subnet mask. Nonetheless, the Solaris installation program and /etc/netmask file require you to set up the subnet mask by using dotted decimal representation. In these ii cases, utilise the dotted decimal representation of the CIDR network prefix, every bit shown in the next table.
Table ii–3 CIDR Prefixes and Their Decimal Equivalent
| CIDR Network Prefix | Bachelor IP Addresses | Dotted Decimal Subnet Equivalent |
|---|---|---|
| /nineteen | 8,192 | 255.255.224.0 |
| /20 | 4,096 | 255.255.240.0 |
| /21 | two,048 | 255.255.248.0 |
| /22 | 1024 | 255.255.252.0 |
| /23 | 512 | 255.255.254.0 |
| /24 | 256 | 255.255.255.0 |
| /25 | 128 | 255.255.255.128 |
| /26 | 64 | 255.255.255.192 |
| /27 | 32 | 255.255.255.224 |
For more information on CIDR addresses, refer to the following sources:
-
For technical details on CIDR, refer to RFC 1519, Classless Inter-Domain Routing (CIDR): an Address Consignment and Aggregation Strategy.
-
More general information nigh CIDR is available from Pacific Bell Internet at Classless Inter-Domain Routing (CIDR) Overview.
-
Another CIDR overview can be establish in the Wikipedia article,"Classless inter-domain routing".
Using Individual IPv4 Addresses
The IANA has reserved iii blocks of IPv4 addresses for companies to use on their private networks. These addresses are divers in RFC 1918, Address Allocation for Individual Internets. Yous tin use these private addresses, also known every bit 1918 addresses, for systems on local networks within a corporate intranet. However, private addresses are not valid on the Internet. Practise not use them on systems that must communicate outside the local network.
| IPv4 Address Range | netmask |
|---|---|
| 10.0.0.0 - ten.255.255.255 | 10.0.0.0 |
| 172.16.0.0 - 172.31.255.255 | 172.xvi.0.0 |
| 192.168.0.0 - 192.168.255.255 | 192.168.0.0 |
How IP Addresses Apply to Network Interfaces
To connect to the network, a arrangement must have at least one physical network interface. Each network interface must have its ain unique IP address. During Solaris installation, you must supply the IP accost for the beginning interface that the installation program finds. Usually that interface has the name device-name0, for example eri0 or hme0. This interface is considered the master network interface.
If you add a second network interface to a host, that interface besides must accept its own unique IP address. When yous add the second network interface, the host and then becomes multihomed. By contrast, when you add a second network interface to a host and enable IP forwarding, that host becomes a router. Meet Configuring an IPv4 Router for an explanation.
Each network interface has a device name, a device driver, and an associated device file in the /devices directory. The network interface might have a device name such every bit eri or smc0, which are device names for two ordinarily used Ethernet interfaces.
For information and tasks related to interfaces, refer to Function I, Administering Single Interfaces, in Arrangement Administration Guide: Network Interfaces and Network Virtualization.
Annotation –
This book assumes that your systems have Ethernet network interfaces. If you programme to use different network media, refer to the manuals that come with the network interface for configuration data.
Naming Entities on Your Network
Subsequently you receive your assigned network IP address and y'all have given the IP addresses to your systems, the side by side task is to assign names to the hosts. So you lot must determine how to handle name services on your network. Yous use these names initially when yous set up your network and later when you expand your network through routers, bridges, or PPP.
The TCP/IP protocols locate a system on a network by using its IP accost. However, if you employ a recognizable proper name, then yous can easily identify the system. Therefore, the TCP/IP protocols (and the Solaris OS) require both the IP address and the host proper noun to uniquely place a organisation.
From a TCP/IP perspective, a network is a set up of named entities. A host is an entity with a name. A router is an entity with a proper noun. The network is an entity with a name. A group or department in which the network is installed can too exist given a name, as can a partition, a region, or a company. In theory, the hierarchy of names that tin be used to identify a network has virtually no limit. The domain proper name identifies a domain.
Administering Host Names
Many sites permit users pick host names for their machines. Servers too require at least one host name, which is associated with the IP address of its primary network interface.
As a system administrator, you must ensure that each host name in your domain is unique. In other words, no two machines on your network tin both have the proper name "fred." Withal, the car "fred" might have multiple IP addresses.
When planning your network, brand a list of IP addresses and their associated host names for easy access during the setup process. The list tin help you verify that all host names are unique.
Selecting a Proper noun Service and Directory Service
The Solaris Os enables you to use three types of name services: local files, NIS, and DNS. Name services maintain critical information almost the machines on a network, such as the host names, IP addresses, Ethernet addresses, and so forth. The Solaris Bone also gives y'all the option of using the LDAP directory service in add-on to or instead of a name service. For an introduction to name services on Solaris, refer to Function I, Nigh Naming and Directory Services, in Organization Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP).
Network Databases
When you install the operating system, y'all supply the host name and IP address of your server, clients, or standalone organization as part of the procedure. The Solaris installation programme adds this data into the hosts This database is part of a set up of network databases that contain information necessary for TCP/IP operation on your network. The name service that you select for your network reads these databases.
The configuration of the network databases is critical. Therefore, y'all need to decide which proper noun service to use equally part of the network planning procedure. Moreover, the decision to use proper noun services also affects whether you lot organize your network into an administrative domain. Network Databases and the nsswitch.conf File has detailed data on the prepare of network databases.
Using NIS or DNS as the Name Service
The NIS and DNS name services maintain network databases on several servers on the network. System Assistants Guide: Naming and Directory Services (DNS, NIS, and LDAP) describes these name services and explains how to configure the databases. In addition, the guide explicate the "namespace" and "administrative domain" concepts in detail.
Using Local Files every bit the Name Service
If you do not implement NIS, LDAP, or DNS, the network uses local files to provide the name service. The term "local files" refers to the series of files in the /etc directory that the network databases utilise. The procedures in this volume presume y'all are using local files for your name service, unless otherwise indicated.
Note –
If yous determine to use local files as the name service for your network, yous can ready upward some other name service at a later appointment.
Domain Names
Many networks organize their hosts and routers into a hierarchy of administrative domains. If you are using the NIS or DNS proper noun service, you lot must select a domain proper noun for your organization that is unique worldwide. To ensure that your domain proper name is unique, you should register the domain name with the InterNIC. If you program to use DNS, you also need to register your domain name with the InterNIC.
The domain name structure is hierarchical. A new domain typically is located beneath an existing, related domain. For case, the domain name for a subsidiary company can be located below the domain of the parent company. If the domain proper name has no other relationship, an system can place its domain proper name directly under one of the existing top-level domains.
The following are a few examples of top-level domains:
-
.com – Commercial companies (international in scope)
-
.edu – Educational institutions (international in scope)
-
.gov – U.Southward. regime agencies
-
.fr – France
You select the name that identifies your organization, with the provision that the proper name must be unique.
Authoritative Subdivisions
The question of administrative subdivisions deals with matters of size and command. The more than hosts and servers that you have in a network, the more complex your management chore. Yous might want to handle such situations by setting upwards additional administrative divisions. Add networks of a item class. Divide existing networks into subnets. The decision about setting upward authoritative subdivisions for your network is determined past the following factors:
-
How big is the network?
A unmarried administrative division can handle a single network of several hundred hosts, all in the same concrete location and requiring the same authoritative services. However, sometimes you should constitute several administrative subdivisions. Subdivisions are particularly useful if you have a small network with subnets and the network is scattered over an all-encompassing geographical surface area.
-
Exercise users on the network have similar needs?
For example, yous might accept a network that is confined to a single edifice and supports a relatively small-scale number of machines. These machines are divided among a number of subnetworks. Each subnetwork supports groups of users with different needs. In this example, you might use an administrative subdivision for each subnet.
Planning for Routers on Your Network
Recall that in TCP/IP, two types of entities exist on a network: hosts and routers. All networks must have hosts, while not all networks crave routers. The physical topology of the network determines if you need routers. This department introduces the concepts of network topology and routing. These concepts are of import when you make up one's mind to add another network to your existing network surround.
Note –
For consummate details and tasks for router configuration on IPv4 networks, refer to Parcel Forwarding and Routing on IPv4 Networks. For complete details and tasks for router configuration on IPv6 networks, refer to Configuring an IPv6 Router.
Network Topology Overview
Network topology describes how networks fit together. Routers are the entities that connect networks to each other. A router is any machine that has ii or more network interfaces and implements IP forwarding. However, the system cannot part as a router until properly configured, as described in Configuring an IPv4 Router.
Routers connect two or more networks to class larger internetworks. The routers must be configured to laissez passer packets between two side by side networks. The routers too should be able to pass packets to networks that lie beyond the adjacent networks.
The following figure shows the bones parts of a network topology. The first illustration shows a uncomplicated configuration of 2 networks that are connected by a single router. The 2d analogy shows a configuration of three networks, interconnected past 2 routers. In the first example, Router R joins Network 1 and Network two into a larger internetwork. In the second example, Router R1 connects Networks 1 and ii. Router R2 connects Networks 2 and 3. The connections form a network that includes Networks i, 2, and 3.
Figure 2–iii Basic Network Topology
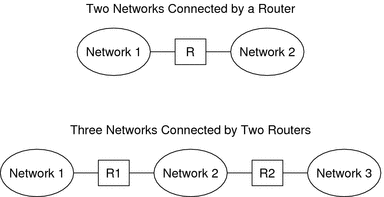
In addition to joining networks into internetworks, routers route packets between networks that are based on the addresses of the destination network. As internetworks grow more than complex, each router must brand more and more decisions well-nigh the packet destinations.
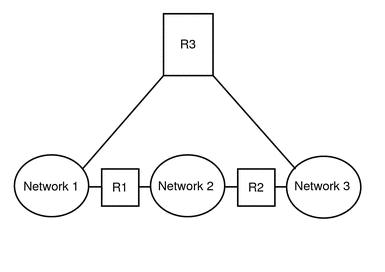
The following effigy shows a more complex case. Router R3 directly connects networks 1 and three. The redundancy improves reliability. If network two goes down, router R3 still provides a route between networks ane and 3. Y'all can interconnect many networks. Still, the networks must use the aforementioned network protocols.
Effigy two–4 A Network Topology That Provides an Boosted Path Between Networks
How Routers Transfer Packets
The IP address of the recipient, which is a role of the bundle header, determines how the package is routed. If this accost includes the network number of the local network, the packet goes directly to the host with that IP address. If the network number is not the local network, the package goes to the router on the local network.
Routers maintain routing information in routing tables. These tables contain the IP accost of the hosts and routers on the networks to which the router is continued. The tables also contain pointers to these networks. When a router receives a package, the router checks its routing table to determine if the tabular array lists the destination address in the header. If the table does non contain the destination accost, the router forwards the package to another router that is listed in its routing tabular array. Refer to Configuring an IPv4 Router for detailed information on routers.
The post-obit effigy shows a network topology with three networks that are connected by two routers.
Figure 2–v A Network Topology With Three Interconnected Networks
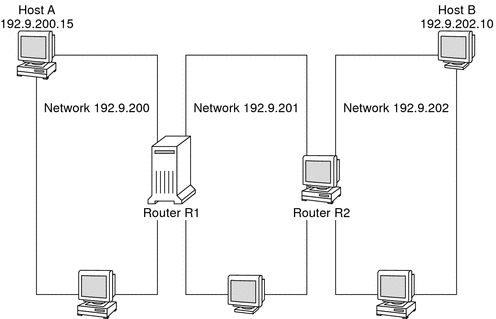
Router R1 connects networks 192.ix.200 and 192.9.201. Router R2 connects networks 192.nine.201 and 192.9.202. If Host A on network 192.ix.200 sends a message to Host B on network 192.9.202, the following events occur:
-
Host A sends a packet out over network 192.9.200. The packet header contains the IPv4 accost of the recipient Host B, 192.9.202.ten.
-
None of the machines on network 192.9.200 has the IPv4 address 192.9.202.10. Therefore, Router R1 accepts the packet.
-
Router R1 examines its routing tables. No automobile on network 192.ix.201 has the address 192.9.202.10. However, the routing tables practice list Router R2.
-
R1 then selects R2 as the "next hop" Router. R1 sends the packet to R2.
-
Because R2 connects network 192.9.201 to 192.nine.202, R2 has routing information for Host B. Router R2 then forwards the packet to network 192.9.202, where Host B accepts the packet.
schumacherdides1938.blogspot.com
Source: https://docs.oracle.com/cd/E19120-01/open.solaris/819-3000/6n58i72ir/index.html
0 Response to "Review the Ipv6 Addressing Scheme Used in the Network Shown in the Following Figure"
Post a Comment